. This will be your primary space for manipulating and analyzing binaries, and it’s where the assembly code resides.) and text. To switch between modes, press the spacebar. displays the text mode view of a disassembled function. It displays the memory address (0040105B) and section name (.text) in which the opcodes (83EC18) will reside in memory ❶.
The left portion of the text-mode display is known as the arrows window and shows the program’s nonlinear flow. Solid lines mark unconditional jumps, and dashed lines mark conditional jumps. Arrows facing up indicate a loop. The example includes the stack layout for the function at ❷ and a comment (beginning with a semicolon) that was automatically added by IDA Pro ❸.
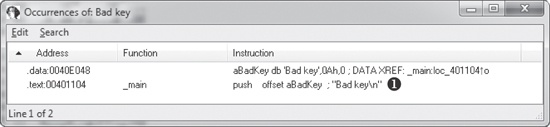
. Double-clicking any of these links ❶ will display the target location in the disassembly window., make it easy to move through your history, just as you would move through a history of web pages in a browser. Each time you navigate to a new location within the disassembly window, that location is added to your history.. We notice that Bad key is used at 0x401104 ❶, so we jump to that location in the disassembly window by double-clicking the entry in the search window.The disassembly listing around the location of 0x401104 is shown next. Looking through the listing, before "Bad key\n", we see a comparison at 0x4010F1, which tests the result of a strcmp. One of the parameters to the strcmp is the string, and likely password, $mab.
004010E0 push offset aMab ; "$mab" 004010E5 lea ecx, [ebp+var_1C] 004010E8 push ecx 004010E9 call strcmp 004010EE add esp, 8 004010F1 test eax, eax 004010F3 jnz short loc_401104 004010F5 push offset aKeyAccepted ; "Key Accepted!\n" 004010FA call printf 004010FF add esp, 4 00401102 jmp short loc_401118 00401104 loc_401104 ; CODE XREF: _main+53j 00401104 push offset aBadKey ; "Bad key\n" 00401109 call printf
The next example shows the result of entering the password we discovered, $mab, and the program prints a different result.
C:\>password.exe Enter password for this Malware: $mab Key Accepted! The malware has been unlocked
This example demonstrates how quickly you can use the search feature and links to get information about a binary.
Назад: Loading an Executable
Дальше: Using Cross-References
) and text. To switch between modes, press the spacebar. displays the text mode view of a disassembled function. It displays the memory address (0040105B) and section name (.text) in which the opcodes (83EC18) will reside in memory ❶.
The left portion of the text-mode display is known as the arrows window and shows the program’s nonlinear flow. Solid lines mark unconditional jumps, and dashed lines mark conditional jumps. Arrows facing up indicate a loop. The example includes the stack layout for the function at ❷ and a comment (beginning with a semicolon) that was automatically added by IDA Pro ❸.
. Double-clicking any of these links ❶ will display the target location in the disassembly window., make it easy to move through your history, just as you would move through a history of web pages in a browser. Each time you navigate to a new location within the disassembly window, that location is added to your history.. We notice that Bad key is used at 0x401104 ❶, so we jump to that location in the disassembly window by double-clicking the entry in the search window.The disassembly listing around the location of 0x401104 is shown next. Looking through the listing, before "Bad key\n", we see a comparison at 0x4010F1, which tests the result of a strcmp. One of the parameters to the strcmp is the string, and likely password, $mab.
004010E0 push offset aMab ; "$mab" 004010E5 lea ecx, [ebp+var_1C] 004010E8 push ecx 004010E9 call strcmp 004010EE add esp, 8 004010F1 test eax, eax 004010F3 jnz short loc_401104 004010F5 push offset aKeyAccepted ; "Key Accepted!\n" 004010FA call printf 004010FF add esp, 4 00401102 jmp short loc_401118 00401104 loc_401104 ; CODE XREF: _main+53j 00401104 push offset aBadKey ; "Bad key\n" 00401109 call printf
The next example shows the result of entering the password we discovered, $mab, and the program prints a different result.
C:\>password.exe Enter password for this Malware: $mab Key Accepted! The malware has been unlocked
This example demonstrates how quickly you can use the search feature and links to get information about a binary.
Назад: Loading an Executable
Дальше: Using Cross-References
displays the text mode view of a disassembled function. It displays the memory address (0040105B) and section name (.text) in which the opcodes (83EC18) will reside in memory ❶.
The left portion of the text-mode display is known as the arrows window and shows the program’s nonlinear flow. Solid lines mark unconditional jumps, and dashed lines mark conditional jumps. Arrows facing up indicate a loop. The example includes the stack layout for the function at ❷ and a comment (beginning with a semicolon) that was automatically added by IDA Pro ❸.
. Double-clicking any of these links ❶ will display the target location in the disassembly window., make it easy to move through your history, just as you would move through a history of web pages in a browser. Each time you navigate to a new location within the disassembly window, that location is added to your history.. We notice that Bad key is used at 0x401104 ❶, so we jump to that location in the disassembly window by double-clicking the entry in the search window.The disassembly listing around the location of 0x401104 is shown next. Looking through the listing, before "Bad key\n", we see a comparison at 0x4010F1, which tests the result of a strcmp. One of the parameters to the strcmp is the string, and likely password, $mab.
004010E0 push offset aMab ; "$mab" 004010E5 lea ecx, [ebp+var_1C] 004010E8 push ecx 004010E9 call strcmp 004010EE add esp, 8 004010F1 test eax, eax 004010F3 jnz short loc_401104 004010F5 push offset aKeyAccepted ; "Key Accepted!\n" 004010FA call printf 004010FF add esp, 4 00401102 jmp short loc_401118 00401104 loc_401104 ; CODE XREF: _main+53j 00401104 push offset aBadKey ; "Bad key\n" 00401109 call printf
The next example shows the result of entering the password we discovered, $mab, and the program prints a different result.
C:\>password.exe Enter password for this Malware: $mab Key Accepted! The malware has been unlocked
This example demonstrates how quickly you can use the search feature and links to get information about a binary.
Назад: Loading an Executable
Дальше: Using Cross-References
Bad key is used at 0x401104 ❶, so we jump to that location in the disassembly window by double-clicking the entry in the search window.The disassembly listing around the location of 0x401104 is shown next. Looking through the listing, before "Bad key\n", we see a comparison at 0x4010F1, which tests the result of a strcmp. One of the parameters to the strcmp is the string, and likely password, $mab.
004010E0 push offset aMab ; "$mab" 004010E5 lea ecx, [ebp+var_1C] 004010E8 push ecx 004010E9 call strcmp 004010EE add esp, 8 004010F1 test eax, eax 004010F3 jnz short loc_401104 004010F5 push offset aKeyAccepted ; "Key Accepted!\n" 004010FA call printf 004010FF add esp, 4 00401102 jmp short loc_401118 00401104 loc_401104 ; CODE XREF: _main+53j 00401104 push offset aBadKey ; "Bad key\n" 00401109 call printf
The next example shows the result of entering the password we discovered, $mab, and the program prints a different result.
C:\>password.exeEnter password for this Malware:$mabKey Accepted! The malware has been unlocked
This example demonstrates how quickly you can use the search feature and links to get information about a binary.