Книга: Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
Назад: The Structure of a Virtual Machine
Дальше: Using Your Malware Analysis Machine
has a list of useful applications for malware analysis.
Next, you’ll install VMware Tools. From the VMware menu, select VM ▶ Install VMware Tools to begin the installation. VMware Tools improves the user experience by making the mouse and keyboard more responsive. It also allows access to shared folders, drag-and-drop file transfer, and various other useful features we’ll discuss in this chapter.
After you’ve installed VMware, it’s time for some configuration.
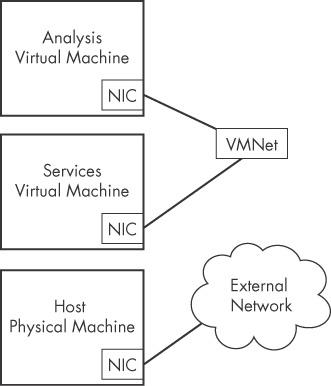
and discussed in the following sections.). illustrates the network configuration for host-only networking. When host-only networking is enabled, VMware creates a virtual network adapter in the host and virtual machines, and connects the two without touching the host’s physical network adapter. The host’s physical network adapter is still connected to the Internet or other external network. shows a custom configuration with two virtual machines connected to each other. In this configuration, one virtual machine is set up to analyze malware, and the second machine provides services. The two virtual machines are connected to the same VMNet virtual switch. In this case, the host machine is still connected to the external network, but not to the machine running the malware.When using more than one virtual machine for analysis, you’ll find it useful to combine the machines as a virtual machine team. When your machines are joined as part of a virtual machine team, you will be able to manage their power and network settings together. To create a new virtual machine team, choose File ▶ New ▶ Team.
illustrates the network configuration for host-only networking. When host-only networking is enabled, VMware creates a virtual network adapter in the host and virtual machines, and connects the two without touching the host’s physical network adapter. The host’s physical network adapter is still connected to the Internet or other external network. shows a custom configuration with two virtual machines connected to each other. In this configuration, one virtual machine is set up to analyze malware, and the second machine provides services. The two virtual machines are connected to the same VMNet virtual switch. In this case, the host machine is still connected to the external network, but not to the machine running the malware.When using more than one virtual machine for analysis, you’ll find it useful to combine the machines as a virtual machine team. When your machines are joined as part of a virtual machine team, you will be able to manage their power and network settings together. To create a new virtual machine team, choose File ▶ New ▶ Team.
When using more than one virtual machine for analysis, you’ll find it useful to combine the machines as a virtual machine team. When your machines are joined as part of a virtual machine team, you will be able to manage their power and network settings together. To create a new virtual machine team, choose File ▶ New ▶ Team.