Книга: Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
Назад: Lab 3-2 Solutions
Дальше: Lab 3-4 Solutions
. (An orphaned process has no parent process listed in the process tree structure.) The fact that svchost.exe is orphaned is highly unusual and highly suspicious., the process appears to be a valid svchost.exe process with PID 388, but this svchost.exe is suspicious because svchost.exe is typically a child of services.exe.From this same properties page, we select Strings to show the strings in both the executable image on disk and in memory. Toggling between the Image and Memory radio buttons shows significant discrepancies between the images. As shown in , the strings in memory on the right contain practicalmalwareanalysis.log and [ENTER], seen at ❶ and ❷, neither of which is found in a typical Windows svchost.exe file on disk, as seen on the left.
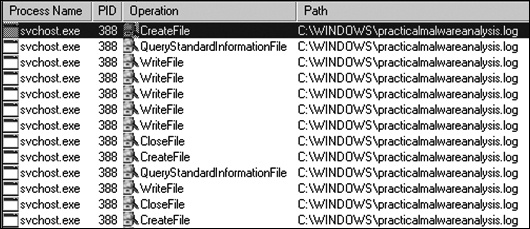
, the CreateFile and WriteFile events for svchost.exe are writing to the file named practicalmalwareanalysis.log. (This same string is visible in the memory view of the orphaned svchost.exe process.)Opening practicalmalwareanalysis.log with a simple text editor reveals the keystrokes you entered in Notepad. We conclude that this malware is a keylogger that uses process replacement on svchost.exe.
Назад: Lab 3-2 Solutions
Дальше: Lab 3-4 Solutions
From this same properties page, we select Strings to show the strings in both the executable image on disk and in memory. Toggling between the Image and Memory radio buttons shows significant discrepancies between the images. As shown in , the strings in memory on the right contain practicalmalwareanalysis.log and [ENTER], seen at ❶ and ❷, neither of which is found in a typical Windows svchost.exe file on disk, as seen on the left.
, the
CreateFile and WriteFile events for svchost.exe are writing to the file named practicalmalwareanalysis.log. (This same string is visible in the memory view of the orphaned svchost.exe process.)Opening practicalmalwareanalysis.log with a simple text editor reveals the keystrokes you entered in Notepad. We conclude that this malware is a keylogger that uses process replacement on svchost.exe.