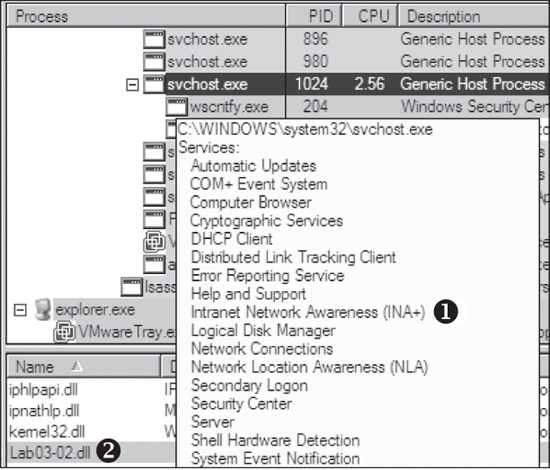
shows that this DLL has five exports, as listed from ❶ and below. The export ServiceMain suggests that this malware needs to be installed as a service in order to run properly.. We enter Lab03-02.dll and click Search. As shown in the figure, the result tells us that Lab03-02.dll is loaded by svchost.exe with the PID 1024. (The specific PID may differ on your system.) shows the result. The display name Intranet Network Awareness (INA+) shown at ❶ confirms that the malware is running in svchost.exe, which is further confirmed when we see at ❷ that Lab03-02.dll is loaded.Next, we turn our attention to our network analysis tools. First, we check ApateDNS to see if the malware performed any DNS requests. The output shows a request for practicalmalwareanalysis.com, which matches the strings listing shown earlier.
Note
It takes 60 seconds after starting the service to see any network traffic (the program does a Sleep(60000) before attempting network access). If the networking connection fails for any reason (for example, you forgot to set up ApateDNS), it waits 10 minutes before attempting to connect again.
We complete our network analysis by examining the Netcat results, as follows:
c:\>nc -l -p 80 GET /serve.html HTTP/1.1 Accept: */* User-Agent: MalwareAnalysis2 Windows XP 6.11 Host: practicalmalwareanalysis.com
We see that the malware performs an HTTP GET request over port 80 (we were listening over port 80 with Netcat since we saw HTTP in the string listing). We run this test several times, and the data appears to be consistent across runs.
We can create a couple of network signatures from this data. Because the malware consistently does a GET request for serve.html, we can use that GET request as a network signature. The malware also uses the User-Agent MalwareAnalysis2 Windows XP 6.11. MalwareAnalysis2 is our malware analysis virtual machine’s name (so this portion of the User-Agent will be different on your machine). The second part of the User-Agent (Windows XP 6.11) is consistent and can be used as a network signature.
Назад: Lab 3-1 Solutions
Дальше: Lab 3-3 Solutions
Intranet Network Awareness (INA+) shown at ❶ confirms that the malware is running in svchost.exe, which is further confirmed when we see at ❷ that Lab03-02.dll is loaded.Next, we turn our attention to our network analysis tools. First, we check ApateDNS to see if the malware performed any DNS requests. The output shows a request for practicalmalwareanalysis.com, which matches the strings listing shown earlier.
Note
It takes 60 seconds after starting the service to see any network traffic (the program does a Sleep(60000) before attempting network access). If the networking connection fails for any reason (for example, you forgot to set up ApateDNS), it waits 10 minutes before attempting to connect again.
We complete our network analysis by examining the Netcat results, as follows:
c:\>nc -l -p 80 GET /serve.html HTTP/1.1 Accept: */* User-Agent: MalwareAnalysis2 Windows XP 6.11 Host: practicalmalwareanalysis.com
We see that the malware performs an HTTP GET request over port 80 (we were listening over port 80 with Netcat since we saw HTTP in the string listing). We run this test several times, and the data appears to be consistent across runs.
We can create a couple of network signatures from this data. Because the malware consistently does a GET request for serve.html, we can use that GET request as a network signature. The malware also uses the User-Agent MalwareAnalysis2 Windows XP 6.11. MalwareAnalysis2 is our malware analysis virtual machine’s name (so this portion of the User-Agent will be different on your machine). The second part of the User-Agent (Windows XP 6.11) is consistent and can be used as a network signature.