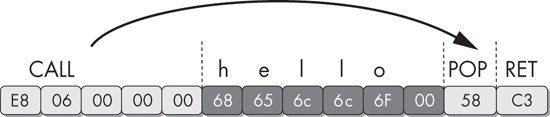
) to implement a crude disassembler in a handful of lines of C using linear disassembly: shows a sequence of bytes and their corresponding machine instructions. Notice the string hello in the middle of the instructions. When the program executes, this string is skipped by the call instruction, and its 6 bytes and NULL terminator are never executed as instructions.
The call instruction is another place where the disassembler must make a decision. The location being called is added to the future disassembly list, along with the location immediately after the call. Just as with the conditional jump instructions, most disassemblers will disassemble the bytes after the call instruction first and the called location later. In handwritten assembly, programmers will often use the call instruction to get a pointer to a fixed piece of data instead of actually calling a subroutine. In this example, the call instruction is used to create a pointer for the string hello on the stack. The pop instruction following the call then takes this value off the top of the stack and puts it into a register (EAX in this case).
When we disassemble this binary with IDA Pro, we see that it has produced disassembly that is not what we expected:
E8 06 00 00 00 call near ptr loc_4011CA+1 68 65 6C 6C 6F ❶push 6F6C6C65h loc_4011CA: 00 58 C3 add [eax-3Dh], blAs it turns out, the first letter of the string hello is the letter h, which is 0x68 in hexadecimal. This is also the opcode of the 5-byte instruction ❶ push DWORD. The null terminator for the hello string turned out to also be the first byte of another legitimate instruction. The flow-oriented disassembler in IDA Pro decided to process the thread of disassembly at ❶ (immediately following the call instruction) before processing the target of the call instruction, and thus produced these two erroneous instructions. Had it processed the target first, it still would have produced the first push instruction, but the instruction following the push would have conflicted with the real instructions it disassembled as a result of the call target.
If IDA Pro produces inaccurate results, you can manually switch bytes from data to instructions or instructions to data by using the C or D keys on the keyboard, as follows:
Pressing the C key turns the cursor location into code.
Pressing the D key turns the cursor location into data.
Here is the same function after manual cleanup:
E8 06 00 00 00 call loc_4011CB 68 65 6C 6C 6F 00 aHello db 'hello',0 loc_4011CB: 58 pop eax C3 retn