Книга: Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
Назад: 10. Kernel Debugging with WinDbg
Дальше: Setting Up Kernel Debugging
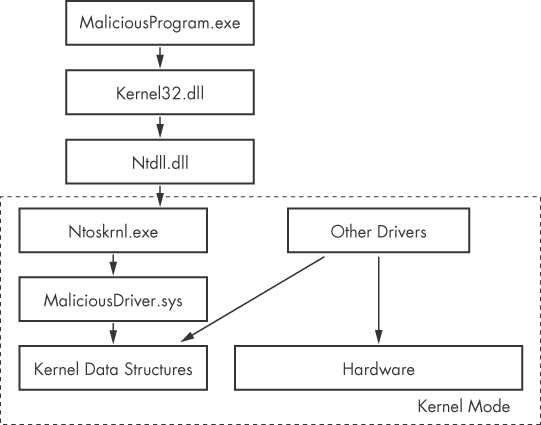
shows how a request from a user-mode application eventually reaches a kernel-mode driver. Requests originate from a user-mode program and eventually reach the kernel. Some requests are sent to drivers that control hardware; others affect only the internal kernel state.
Malicious drivers generally do not usually control hardware; instead, they interact with the main Windows kernel components, ntoskrnl.exe and hal.dll. The ntoskrnl.exe component has the code for the core OS functions, and hal.dll has the code for interacting with the main hardware components. Malware will often import functions from one or both of these files in order to manipulate the kernel.
Назад: 10. Kernel Debugging with WinDbg
Дальше: Setting Up Kernel Debugging